A Vpn Connection Consists of Which of the Following Componen
Each correct answer represents a complete solution. It operates at the Physical layer of theOSl model.
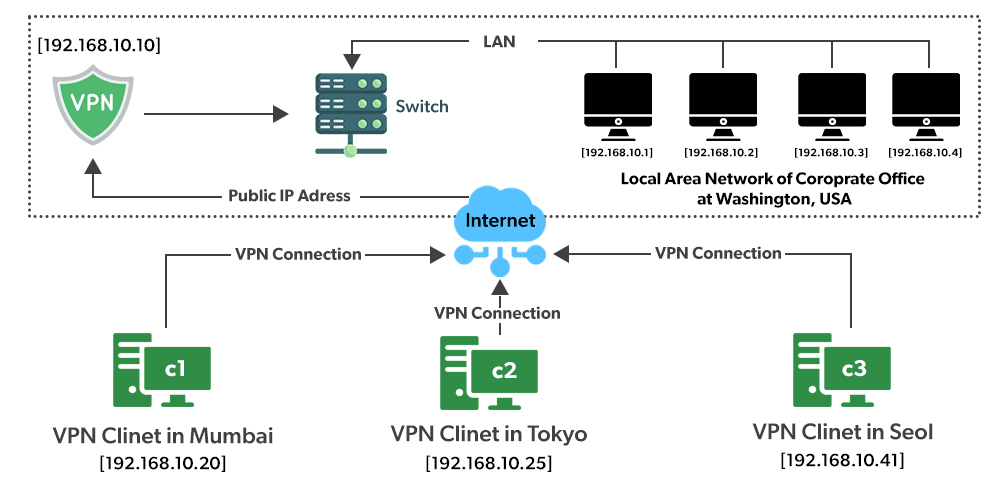
Virtual Private Network Vpn An Introduction Geeksforgeeks
The VPN protocols.
. Communication tunnel between VLANs. Which of the following statements are true about a virtual private network VPN. Encrypted connection across the Internet.
Which of the following techniques makes a VPN private. For more information about Site-to-Site VPN quotas see Site-to. Encrypting and encapsulating traffic.
Either way youd like to know all about the various types of VPNs and wherewhen theyre useful. A physical device or software application on your side of the VPN. What is the primary difference between a VPN connection and a local network connection.
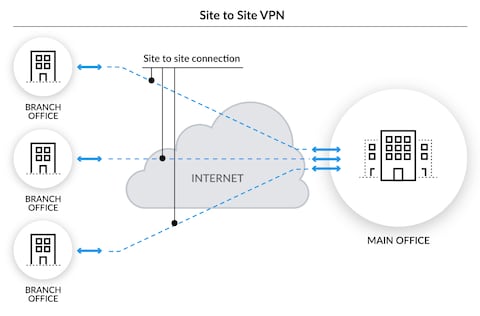
A Site-to-Site VPN connection consists of the following components. SSL Secure Sockets Layer and TLS Transport Layer Security generate a VPN connection where the web browser acts as the client and user access is prohibited to specific applications instead of entire network. Maybe youve been using a VPN service for a while now.
From a computer that runs Windows 10 Pro a user named User1 creates an SSTP VPN connection to a network named VPN1. User Datagram Protocol UDP Transmission Control Protocol TCP Layer 2 Tunneling Protocol L2TP By default your VPN uses the UDP protocol that may be blocked. Choose all that apply.
We would like to show you a description here but the site wont allow us. Note that this exact wording only applies. It uses a terminal adapter to connect to the network.
You can connect your Amazon VPC to remote networks and users using the following VPN connectivity options. Which of the following is true about ISDN. A VPN connection can help provide a more secure connection and access to your companys network and the internet for example when youre working from a coffee shop or similar public place.
On the AWS side of the Site-to-Site VPN connection a virtual private gateway or transit gateway provides two VPN endpoints tunnels for automatic failover. There are several ways protocols in which such a VPN connection can be set up. Extranet-based VPN D.
Or youve just finished our beginners guide and are hungry for more knowledge on VPNs. Virtual network within your local area network LAN. It uses a modem to modulatedemodulate the signal.
The computer containing the VPN connection is actually connected to the network C. This can be caused by a problem in the VPN transmission and is commonly the result of internet latency or simply that your VPN server has reached capacity. Its PRI format provides bandwidth up to 128 Kbps.
Whether its for work or personal use you can connect to a virtual private network VPN on your Windows 10 PC. A VPN relies on network firewalls encryption and other Internet and intranet security features. When User1 roams between different Wi-Fi access points the user loses the connection to the corporate network and must manually re-establish the VPN connection.
You can create an IPsec VPN connection between your VPC and your remote network. A VPN uses the Internet as its main backbone network. A VPN uses the Internet to establish secure intranets between its distant offices and locations.
Remote access VPNs include client-based IPsec VPNs and clientless SSL VPNs. A VPN is aan. Change your VPN Protocol.
Remote access VPN C. Have more security vulnerabilities than software VPNs. It is a network that uses a public telecommunication infrastructure such as the Internet.
Data does not traverse the Internet. You have mobile devices that run Windows 10 and have VPN connection to the VPN server. The computer acts as a dumb terminal D.
Which of the following is a type of VPN connection. Virtual Private Gateway. A Site-to-Site VPN connection offers two VPN tunnels between a virtual private gateway or a transit gateway on the AWS side and a customer gateway which represents a VPN device on the remote on-premises side.
If this problem persists contact the VPN administrator and analyze quality of network connectivity. You need to ensure that when users work remotely and Connect to the VPN only traffic for the corporate network is sent through the VPN server. Site-to-site VPN This VPN is created when interconnecting devices are preconfigured with information to establish a secure tunnel.
Amazon Web Service AWS supports Internet Protocol security IPsec VPN connections. The truth is virtual private networks come in many different shapesIt can be overwhelming to distinguish between the. A VPN protocol is a set of rules that assist in the connection between the VPN client and VPN server.
VPN connections use an encrypted connection also called a tunnel. VPC and your own network. These protocols ensure that your data remains safe and cant be read by others.
Which of the following is NOT true about a hardware VPN. Its BRI format consists of two B-channels and one D-channel. User1 successfully connects to the VPN server.
PPTP VPN B. Personal network for your use only. Please try to reconnect to the VPN server.
Which of the following is true about software VPNs. The domain contains a VPN server that supports all of the VPN protocols. Which of the following types of VPN uses the Internet as its main backbone allowing users customers and branch offices to access corporate network resources across various network architectures.
Best when all router and firewall hardware is the same. Remote Access VPN This VPN is created dynamically when required to establish a secure connection between a client and a VPN server. VPN use different protocols such as.
A single organization owning all the supporting infrastructure components. A VPN connection consists of the following elements. All the following describe a VPN except.
It was discovered that several user accounts belonging to former employees were still active and had valid VPN permissionsWhich of the following would help reduce the amount of risk. The performance characteristics of a VPN supporting remote clients are generally the same as the performance characteristics of a VPN supporting site-to-site connections. False The IPv6 IPSec is a set of national standards that use cryptographic security services to provide confidentiality data origin authentication and data integrity.
Leasing dedicated WAN channels from a telco. A VPN concentrator on Amazon side of the VPN connection.

Vpn Package Page Design Page Design Mobile Design Inspiration Planning App

What Is A Site To Site Vpn Palo Alto Networks

Creating A Fully Redundant Vpn Connection Requires The Setup And Configuration Of Two Vpn Instances And A Aws Architecture Diagram Diagram Diagram Architecture
No comments for "A Vpn Connection Consists of Which of the Following Componen"
Post a Comment